What you will learn
- How bad guys use information already
exists on the net to gain access to:
- your email accounts,
- your financial information such as credit
cards, PayPal accounts etc,
- your internet hosting accounts (if you
have any),
- your personal web sites,
- your personal life in general!
- How you can protect yourself by such bad situations by following some very simple but very efficient security rules.
The actual incident that this article is based
on was 100% real but for privacy reasons all referred user names are not the
real ones and they have been chosen randomly. According to the same reason all
images have been obscured.
The existence of the Internet, among other things, saves us from many tedious tasks as well as speeds up many real life opereations, such as: accounts payments, bank accounts monitoring and checking, purchasing almost all goods (from books to bookstores ...!) from online stores, avoiding going at the post-office for our mails and many others that could easily fill up all the pages of this magazine!
We can do all these amazing, calmly and nicely from the sofa of our home. It is much better than running on roads in cold or heat, in the crowds etc. Is ‘n it? The problem is that these pos have (always) some cons!
In the article we will get the role of a bad guy. We will show how easy is for us to spy someone (even stranger) and to collect, with a minimum of effort, almost all of his/her personal information. In an era, where security of personal data start to concern even public parties, we will show how easily is for a bad guy to gain access to the personal data of another person, such as occupation info, photos, names, family records, personal preferences (hidden and not ;-)), credit cards, accounts numbers, etc.
In addition, we will present how we can easily steal the "identity" of our victim in order to appear on the internet as him or her (see "impersonation" - http://is.gd/f3ha)! Does this remind you something like 007? We assure you that everything presented here is true; it can happen to anyone and we will prove it. But of course, at the end we will give you all the necessary "arsenal" and tips in order to not fall or to be very difficult to fall to such an unpleasant situation.
So, let us begin from Google! One evening we had an appetite for "searching". We get to Google and we start searcing for directories that contain the file classifieds.cgi. We enter something like the following on Google box:
What we get as a result is a fairly long list of sites. We started studying it one by one. After some searching we found a site that allows directory listing. This is not necessarily a security hole but it is a bad security practice. You will never know when a forgetful administrator will leave, in a dark corner of a directory, a file full of username and passwords or emails (Figure 1)!
 |
| Figure 1: When admin is forgetful, users are the victims! |
Um ... what we have here? We have a list of usernames and passwords with their email. Ok, by using this information we can only impersonate a user of the current site. But, this is not enough. We want to try our theory which is this: many users use the same password for their favorite sites (forums etc.) and their email account too!
Let’s check our assumption: We check the file defaul.users, for all users with a yahoo email and we start trying every single of them to enter to his/her email using as password the one displayed in this file. Incidentally, the third user to the series is "vulnerable" to our theory (Figure 2). To be specific, we found that an approximately 50% of users fall into this “trap”.
 |
| Figure 2: Our victim Mrs. Mary and ... her email! |
Search for mails to welcome the victim as a new member in a forum. In such mails usually user credentials are presented. One such email is displayed at Figure 3.
 |
| Figure 3:Username and Password to login to a forum! |
In addition, we found a very interesting group of information titled "View Profile". This is the personal details of Mrs. Mary along with her photo! In the same location, we found her CV along with phone numbers, addresses and names of friends and relatives (Fig. 4).
 |
| Figure 4: The personal data of our "victim"! |
While we are talking about spam and spammers, we should not omit to mention this: the joy of the spammer is to "dive" into a sea of real emails. Once again, aiming for profit, we can extract and sell a short list of about 100 emails (real names included!) we found in the account of the indeed very popular Mrs. Mary (Figure 4b).
 |
| Figure 4b: A "gift" to the spammers! |
 |
| Figure 5: Domain names and the corresponding DNS Servers. |
If we are really bad, we can change the password of every domain she owns in order to lock her out and then redirect the DNS servers to make a deface (at least) or to increase the traffic of another site!
But ... just a minute! There is something more serious here: a ‘My Wallet’ option. Getting there we have the credit card of Mrs. Mary. Ok, this is not the full number but we have all of her data (area, phone, city etc.) that is very useful information (Figure 6). As you can see the connection, is a secure one (ssl). Very secure... indeed ;)
 |
| Figure 6: And the credit card info |
And now we come to the most evil part of our search. In the yahoo-mail there is a very useful button that is called "Search". By pressing it, we can find a string that appears in one or more emails. We can search for any word we like. We have chosen the word “PayPal”. For those who do not “remember” PayPal is a service on the internet that connects to your bank account or your credit card with which you can make purchases by giving only a PayPal user code. To be honest, we must say that we found many emails referring a PayPal account, but no password information was available. Um ... actually we don’t need it! What we can do is go to PayPal and choose the functionality “I forgot my password” (Figure 7)!
 |
| Figure 7: Tricking the PayPal ... |
Immediately PayPal send in the Mary’s email a new password assuming that Mrs. Mary is the only one that has access to her mail. What a wrong assumption! Now, we can buy goods with Mrs. Mary’s credit card. Fair enough, don’t you thing?!
We can do many more things but let's stop here. We "played" enough with Ms. Mary. Let's try another yahoo mail that we found in our early list. Maybe our luck is still “active” (Fig. 8).
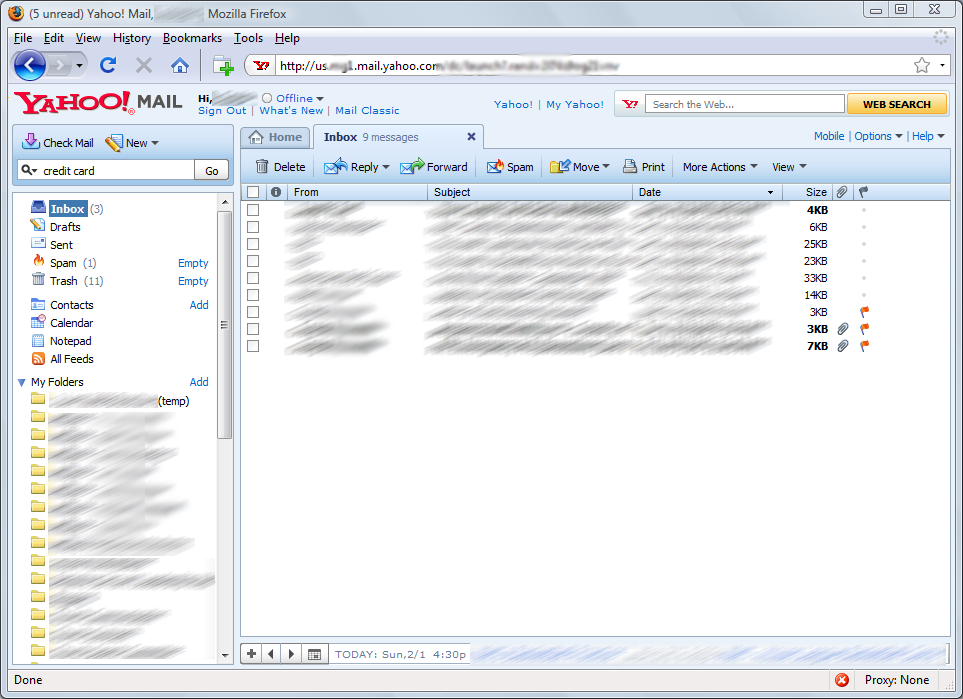 |
| Figure 8: Hello Alan ...! |
Hello Mr. Alan! We are ready to uncover your secrets! History repeats itself.
Conclusions and protection
We presented a
very simple method that a bad guy can violate the privacy (and also the
personal life) of another person by getting access to his/her personal
information simply because some administrator was stupid enough to let a data file
with sensitive info in a directory accessible from the web. You may ask "Well well! All my private life is on the
hands of any stupid admin? “. The answer is: Unfortunately yes, if you do
not follow some basic safety rules. If you choose to have the same password on your
favorite forum with what you have to access your bank account then do not blame
SSL if you suddenly see a 2000euro bill for your new journey to Seychelles!
So pay full attention to a few small but golden rules to avoid unpleasant surprises.
So pay full attention to a few small but golden rules to avoid unpleasant surprises.
- Rule 1.
Do not be "ashamed" to use multiple passwords! If you have difficulties to remember them, use a Password Manager (there are many free that you can download from the net). Personally, I prefer KeePass (you can download it from http://keepass.info/). It is a free standalone application that can be run on the user’s box. It uses strong encryption (AES, Twofish) and can functions well on both Linux and Windows. In addition, has many handy features, such as web form auto fill, strong random password generator etc.
- Rule 2.
Use at least two emails: One for the public sites (forums etc.) and one for your personal and financial account sites.
- Rule 3.
Choose a strong password. Strong passwords are those that are longer than 15 characters (ok, and smaller than 100!) and contain lowercase, uppercase, numbers and special characters such as “!@#$%^&*()_+-='”.
- Rule 4.
Always delete your emails that contain username and passwords of any web service you registered. Remember to real delete them. We mean, delete them from your inbox (or any subfolder) and from any trash-can that they may be putted after the deletion.
- Rule 5.
When you finish with your financial web tasks always logout from the corresponding site and clear the cache (delete history) of your web browser.
Finally, never forget the general rule in computer security (and not only):
The chain is as strong as its weakest link.
Safe Surfing!!

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.